govulncheck-action: Adding the initial version of the govulncheck github action & README
Change-Id: I1e5ea64b91d6f10147c0632441df189de5e486b3
Reviewed-on: https://go-review.googlesource.com/c/govulncheck-action/+/494038
Reviewed-by: Brandon Kessler <bkessler@google.com>
Auto-Submit: Brandon Kessler <bkessler@google.com>
TryBot-Bypass: Brandon Kessler <bkessler@google.com>
Reviewed-by: Julie Qiu <julieqiu@google.com>
Run-TryBot: Brandon Kessler <bkessler@google.com>
diff --git a/README.md b/README.md
index d209cac..8ac2263 100644
--- a/README.md
+++ b/README.md
@@ -1,6 +1,50 @@
-# GitHub action for govulncheck
+# GitHub Action for govulncheck
-This repository holds the GitHub action for govulncheck code.
+This repository holds the GitHub Action for govulncheck. Govulncheck reports known vulnerabilities that affect Go code. It uses static analysis of source code or a binary's symbol table to narrow down reports to only those that could affect the application. You can read more about govulncheck at https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck.
+
+The govulncheck GitHub Action is currently experimental and is under active development.
+
+## Using the govulncheck GitHub Action
+
+To use the govulncheck GitHub Action add the following step to your workflow:
+
+```yaml
+- id: govulncheck
+ uses: golang/govulncheck-action@v1
+```
+
+By default the govulncheck Github Action will run with the latest version of Go using the ./... package path:
+
+```govulncheck ./...```
+
+If you would like to specify a specific version of Go to use or a different package path to run govulncheck against then you can do so by adding the following step to your workflow:
+
+```yaml
+- id: govulncheck
+ uses: golang/govulncheck-action@v1
+ with:
+ go-version-input: 1.XX
+ go-package: ./...
+```
+
+Below is a full example of a workflow that runs govulncheck against a simple repository on every push:
+
+```yaml
+on: [push]
+
+jobs:
+ govulncheck_job:
+ runs-on: ubuntu-latest
+ name: Run govulncheck
+ steps:
+ - id: govulncheck
+ uses: golang/govulncheck-action@v1
+ with:
+ go-version-input: 1.20.3
+```
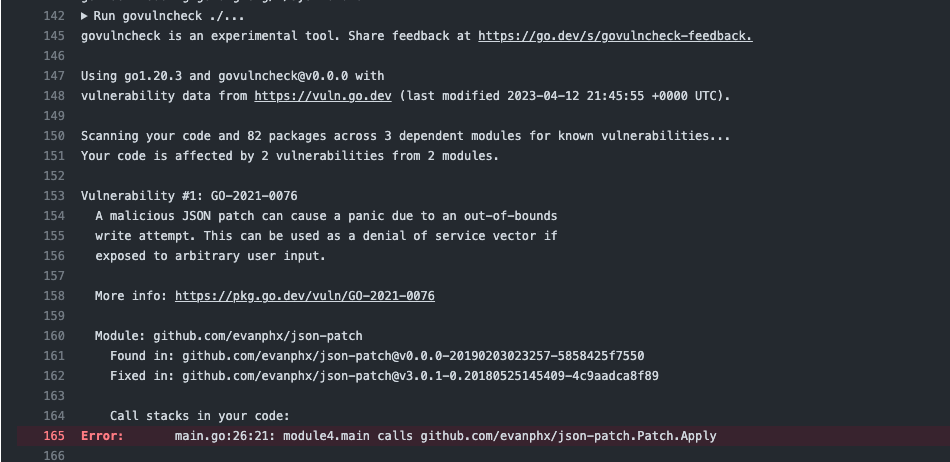
+When this workflow finds a vulnerability you will see an error in the Run govulncheck job like the one below. The output contains information about the vulnerability and how to fix it:
+
+
## Report Issues / Send Patches
diff --git a/action.yml b/action.yml
new file mode 100644
index 0000000..a46751b
--- /dev/null
+++ b/action.yml
@@ -0,0 +1,24 @@
+name: 'govulncheck'
+description: 'Run govulncheck'
+inputs:
+ go-version-input: # version of Go to use for govulncheck
+ description: 'Version of Go to use for govulncheck'
+ required: false
+ default: '>=1.19.0'
+ go-package:
+ description: 'Go Package to scan with govulncheck'
+ required: false
+ default: './...'
+runs:
+ using: "composite"
+ steps:
+ - uses: actions/checkout@v3
+ - uses: actions/setup-go@v4.0.0
+ with:
+ go-version: ${{ inputs.go-version-input }}
+ - name: Install govulncheck
+ run: go install golang.org/x/vuln/cmd/govulncheck@latest
+ shell: bash
+ - name: Run govulncheck
+ run: govulncheck ${{ inputs.go-package }}
+ shell: bash