README.md: wrap text
Change-Id: Ic440b5168ecf73bf739373bcbbc3af36273b9951
Reviewed-on: https://go-review.googlesource.com/c/govulncheck-action/+/496877
Reviewed-by: Brandon Kessler <bkessler@google.com>
Reviewed-by: Julie Qiu <julie@golang.org>
TryBot-Bypass: Julie Qiu <julie@golang.org>
Reviewed-by: Julie Qiu <julieqiu@google.com>
diff --git a/README.md b/README.md
index 8ac2263..f2596aa 100644
--- a/README.md
+++ b/README.md
@@ -1,8 +1,13 @@
# GitHub Action for govulncheck
-This repository holds the GitHub Action for govulncheck. Govulncheck reports known vulnerabilities that affect Go code. It uses static analysis of source code or a binary's symbol table to narrow down reports to only those that could affect the application. You can read more about govulncheck at https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck.
+This repository holds the GitHub Action for govulncheck. Govulncheck reports
+known vulnerabilities that affect Go code. It uses static analysis of source
+code or a binary's symbol table to narrow down reports to only those that could
+affect the application. You can read more about govulncheck at
+https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck.
-The govulncheck GitHub Action is currently experimental and is under active development.
+The govulncheck GitHub Action is currently experimental and is under active
+development.
## Using the govulncheck GitHub Action
@@ -13,11 +18,14 @@
uses: golang/govulncheck-action@v1
```
-By default the govulncheck Github Action will run with the latest version of Go using the ./... package path:
+By default the govulncheck Github Action will run with the latest version of Go
+using the ./... package path:
```govulncheck ./...```
-If you would like to specify a specific version of Go to use or a different package path to run govulncheck against then you can do so by adding the following step to your workflow:
+If you would like to specify a specific version of Go to use or a different
+package path to run govulncheck against then you can do so by adding the
+following step to your workflow:
```yaml
- id: govulncheck
@@ -27,7 +35,8 @@
go-package: ./...
```
-Below is a full example of a workflow that runs govulncheck against a simple repository on every push:
+Below is a full example of a workflow that runs govulncheck against a simple
+repository on every push:
```yaml
on: [push]
@@ -42,7 +51,9 @@
with:
go-version-input: 1.20.3
```
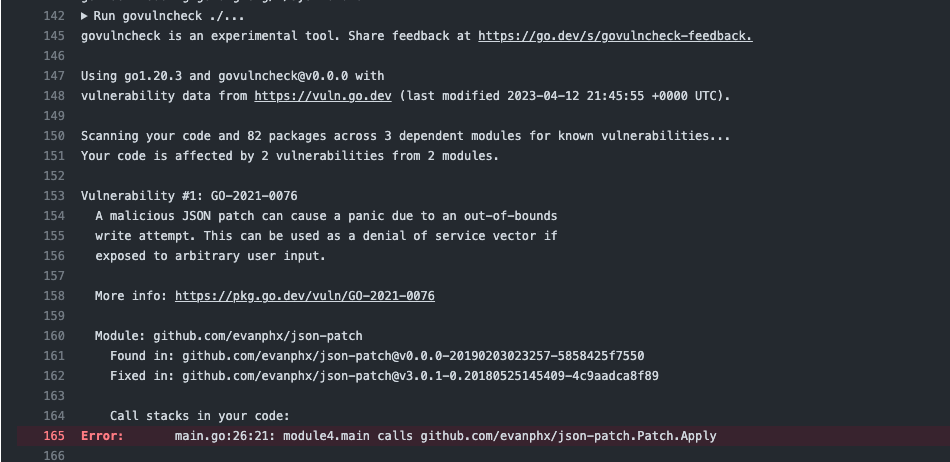
-When this workflow finds a vulnerability you will see an error in the Run govulncheck job like the one below. The output contains information about the vulnerability and how to fix it:
+When this workflow finds a vulnerability you will see an error in the Run
+govulncheck job like the one below. The output contains information about the
+vulnerability and how to fix it:
@@ -52,5 +63,5 @@
this repository, see https://go.dev/doc/contribute.html.
The main issue tracker for the time repository is located at
-https://github.com/golang/go/issues. Prefix your issue with "x/govulncheck-action:" in the
-subject line, so it is easy to find.
+https://github.com/golang/go/issues. Prefix your issue with
+"x/govulncheck-action:" in the subject line, so it is easy to find.